O2 were next on the list for a tear-down of their filtering anyway but as luck would have it they blocked RoutingPacketsIsNotACrime.uk which meant I had control of both ends of a TCP/HTTP connection that was being filtered. Being able to investigate what happens from both sides is an opportunity that is too good to miss.
You can buy an O2 PAYG device such as a phone, dongle or MiFi in cash and with a name that doesn’t require verification.
This will however result in you receiving a SIM with the “Default Safety” level of filtering enabled. Attempting to visit legitimate, non-sexual and legal websites such as RoutingPacketsIsNotACrime.uk can result in a block page;
The good news is that the O2 filters are quite easy to circumnavigate.
DNS Spoofing: No
MiTM SSL: No
Deep Packet Inspection: Partial
Destination IP Transit Interference: Yes
-
Unique Reason for Block: No
Categorised Block: No
Ability to report incorrect block: No
Tor
The goto advice is, as always, to download Tor as it will not only bypass all filtering but will also help mask those who need to use Tor to aid in protecting their privacy if configured as a relay too.
With Tor installed and configured to listen on port 9050 as a SOCKS proxy (or using the bundled Tor Browser if using the Tor Bundle or the Android port Orbot) you will be able to bypass all filtering (including the censored blocks forced on you even if you are over 18)
SOCKS5 SSH Proxy
If you don’t want to use Tor then creating a SOCKS tunnel via SSH is also an excellent option. Visit LowEndBox.com where you can get tiny cloud servers (e.g. 128Mb of RAM) for as little as £5 a year that can be paid for in advance with a prepaid Visa/Mastercard.
Once you’ve purchased or otherwise acquired a server running OpenSSH (or any other variety that supports tunneling) simply connect to it specifying the -D option to create a local dynamic tunnel;
ssh -D 9050 proxy1.survivetheclaireperryinter.net
Once connected you can configure your browser to use 127.0.0.1 port 9050 as a SOCKS5 proxy (Edit – Preferences > Network > Settings > SOCKS Host) and bypass all filtering.
SSL
O2 cannot Man in the Middle (MiTM) SSL connections so any website that has an SSL component and not yet subject to a High Court Order block is accessible over SSL.
This also means that you can use a RoutingPacketsIsNotACrime.uk PAC file to get around all filtering despite them banning the HTTP path.
Attacking from Both Sides
Since this is the first time I’ve had access to both sides of the filtering fence I can examine what is happening to our packets to see how O2′s filtering works.
A first attempt at connecting provides the attached packet capture where we can see that our host (OpenBSD) does a DNS lookup for both the A and the AAAA record. The MiFi dongle returns the correct IP addresses for both queries indicating that there isn’t any Nominum style DNS interference going on.
Packet 5 is the start of the HTTP sequence and everything is going fine, in packet 8 curl sends the host header we’re after, at this point there’s a rogue TLSv1 encrypted connection to 185.29.44.9 (o2bb.winint.net and mobilebroadbandaccess.o2.co.uk – we’ll delve into this later) which is from an earlier session.
Packet 11 appears to be an ACK from my server in response to packet 8 however packets 12 and 13 shows that the server sent a 302 redirect to send the browser to http://assets.o2.co.uk/18plusaccess. Well we know that this isn’t true. Interestingly we then get some packets (16,17 and 19) that Wireshark flags as out of order and duplicate responses to the earlier packets.
From this we can make a couple of assumptions, the first that O2′s filtering system relies on a deep packet or proxy inspection of the host header and secondly that there is possibly a race condition for returning HTTP packets.
Hacking RFCs
RFC 2616 section 14.23 dictates that a valid HTTP/1.1 request will contain a host header but doesn’t specify how many (for obvious reasons), so lets see if we can abuse this by manipulating the HTTP headers using curl e.g;
curl 89.151.84.121 -H 'Host: o2-censor.com' -H 'routingpacketsisnotacrime.uk'
The HTTP request is allowed through without issue however the web server at the other end will also ignore the second Host header and attempt to serve the first.
Passing the first host header as an empty string and the second as the host we want results in a block. Maybe we’ll come back to this later (custom build of apache + browser plugin?).
The next test is to see if there is coupling between the IP and HTTP host.
curl 46.4.22.9 -H 'routingpacketsisnotacrime.uk'
Still results in a block. OK, well we know that O2 can’t interfere with 443, it’s possible that they see the cypto handshake or that they see it’s not port 80 and ignore it so I tried setting an apache host to listen on 8081 but the Host header was still detected and blocked.
On a whim I tried using a RoutingPacketsIsNotACrime.uk PAC file served over SSL and that worked which was a relief.
Anyhow, back to messing with host headers. Since we know that O2 rely on the Host header lets set a rubbish DNS name in /etc/hosts (or C:\windows\system32\drivers\etc\hosts for you Windows people) and configure apache to serve the censored website on a given IP regardless of host header (a default vhost if you will).
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4 ::1 localhost localhost.localdomain localhost6 localhost6.localdomain6 89.151.84.121 routingpacketsisgreat.fucko2
Success! As you can see in packet 4 of this Wireshark packet capture we sent a Host header of routingpacketsisgreat.fucko2 and received the correct response back from the server which is a 302 to https://RoutingPacketsIsNotACrime.uk and since we know that SSL is not interfered with the connection continues.
For completeness sake lets see what a censored connection looks like from the server side.
When sending a HTTP GET to wtfismyip.com the IP returned was consistently 82.132.245.233 however as we can see from the packet capture the IP that reached out to my server was 82.132.245.111. It starts the first part of the TCP handshake and then sends a TCP reset.
From within the O2 network this server appears to be listening on thousands of ports whereas from an outside source it appears that there are no listening ports.
All servers within the 82.132.244.0/24 have a PTR record of dab-rcn1-h-xx-3.dab.02.net where xx does increase with each IP but does not correlate to the IP itself.
There appears to be a limited form of session or IP ‘stickiness’ with repeated connections to differing remote IPs always coming from the same host (e.g. a.b.c.d ‘sticks’ to dab-rcn1-h-ab-3.dab.02.net but e.f.g.h ‘sticks’ to dab-rcn1-h-xy-3.dab.02.net).I didn’t test the longevity of the stickiness but it doesn’t really matter.
Using our fake Host header trick the connection completes but still comes from the 82.132.245.0/24 range (although in other captures I’ve seen 82.132.244.0/24). So it would appear that these proxies will evaluate all plain text traffic regardless of whether the IP is known to host blocked content.
The TCP dump indicates that whilst the initial TCP handshake happens the upper layer (HTTP) doesn’t until the proxy has evaluated the host header which means the second assumption about a possible race condition was incorrect.
StreamShield
As an interesting aside by evaluating how the server responds to certain requests it’s fairly likely that these filtering boxes are running some form of Linux, that conclusion is further strengthened by the fact that BAE is hiring Linux C++ engineers for their StreamShield product which we know from Court documents is what O2 use.
 The BAE StreamShield system is quite nasty, enabling real time deep packet inspection of various protocols (which is how it picks out the host header from HTTP streams) but can also do real time filtering based on the content of the returned data.
The BAE StreamShield system is quite nasty, enabling real time deep packet inspection of various protocols (which is how it picks out the host header from HTTP streams) but can also do real time filtering based on the content of the returned data.
It also gathers and stores all that information about you so that O2 can hand over details about what you’ve been doing to anyone who asks thanks to the Data Retention and Investigatory Powers Act.
Returning to 185.29.44.9
This IP block belongs to a company called IMIMOBILE EUROPE LTD who appear to be in the business of monetizing mobile customers through a variety of means.
185.29.44.9 is mobilebroadbandaccess.o2.co.uk and is part of a joint venture between the two to create self service portals.
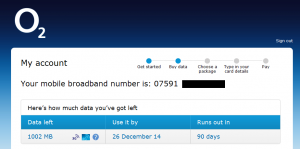
Interestingly you can put any O2 phone number in, from any Internet connection (including Tor) and it will divulge a limited amount of information about the account.
Little though the information may be, with scams such as the “Microsoft Event View Tech Support” or “Compromised Bank Card key in your Pin” call it is dangerous to tell the wrong people when another persons PAYG SIM expires and how much data is left, vulnerable people can be convinced with less. But then again, we’re talking about the company that censored the NSPCC and ChildLine websites so looking after vulnerable people isn’t top of their priorities.
So, I’m down another £40 but it’s been very interesting to play with O2′s censorship technology which, it turns out, is easy to circumnavigate because the ‘Net interprets censorship as damage and routes around it.
To prohibit the reading of certain books is to declare the inhabitants to be either fools or slavesClaude Adrien Helvétius